Protect Your Business from Cyber Threats with a Partner You Can Trust
At RPM Computing, we understand that modern businesses face a growing number of digital threats—from ransomware and phishing attacks to insider risks and compliance challenges. Our full suite of cybersecurity services is designed to protect your business without overwhelming your team or breaking your budget.
We deliver technology that works — so your team can too. From proactive support to business continuity and security, our services are designed to grow with you.
Secure every device—laptops, desktops, and mobile—with industry-leading antivirus, EDR (Endpoint Detection & Response), and real-time threat monitoring.
We install and manage firewalls, intrusion prevention systems, and secure remote access to keep your network locked down and your data safe.
Your employees are your first line of defense. We deliver practical, engaging training and phishing simulations to reduce human error and improve security culture.
Protect Microsoft 365, Gmail, and cloud applications from spoofing, malware, and unauthorized access with advanced filters and zero-trust policies.
Need to meet HIPAA, PCI, or CMMC requirements? We conduct audits, remediate vulnerabilities, and provide the documentation you need for peace of mind—and pass your next audit.
If a breach occurs, we act fast. Our team investigates, contains the threat, and helps restore your systems and reputation with minimal downtime.
Every business is different. We start with a cybersecurity risk assessment and tailor our recommendations to your industry, risk level, and budget. Whether you need basic protection or a full-stack security solution, we’ll build a plan that fits.
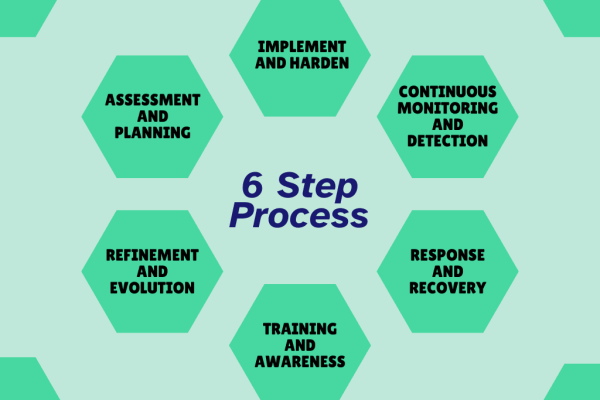
Securing a business’s technology involves a multi-phased approach that aligns with strategic objectives to safeguard digital assets, ensure operational continuity, and comply with regulatory requirements. Below is an overview of the essential phases to securing a business’s technology:
Based in Huntsville, Alabama, RPM Computing proudly supports local businesses and remote teams across the U.S. with scalable, high-value cybersecurity solutions.







Not sure where to begin? We’ll take a look under the hood — from your infrastructure to your cybersecurity risks to your readiness for AI integration — and give you clear next steps.
No pressure. No jargon. Just real insight.